ESET Mail Security provides Linux, BSD & Solaris based mail servers with effective protection from known
and emerging forms of malware including viruses, worms, Trojans, and other Internet security threats.
Safeguard your Linux, BSD & Solaris file servers with ESET File Security‘s real-time protection from known and emerging threats.
ESET NOD32 Antivirus 4 for Linux Desktop provides complete endpoint protection against cross-platform and emerging threats.
OK, guys, let’s try out how ESET security solutions will work on CentOS 6.3 x86_64 server and protect the server itself and its users.
System used:
- Platform: VirtualBox
- Operating system: CentOS 6.3 x86_64
- Desktop environment: XFCE 4
- Hosting control panel: ISPconfig 3
- Web server: nginx
- Mail server: Postfix
- Mail Delivery Agent (MDA): maildrop
- Server name: post.example.com
- IP address: 192.168.0.45
- Same ESETS (ESET Security) installation will work for Mail, Gateway and File security solutions. You can use them all together or separately as long as you own corresponding licences. To obtain a licence(s) for ESET software please visit our e-shop or simply contact us.
Table of contents:
- Installing CentOS 6 XFCE mini server
- Installing ESET NOD32 4
- ESET Mail Security installation and configuration
- ESET File Security configuration
I used a minimal image to install CentOS 6.3 on VirtualBox virtual machine.
Installing and configuring CentOS 6.3 XFCE mini server
Firstly install CentOS 6.3 on your machine from minimal iso image. Only a few steps are involved doing it so I will not cover them in this article.
Once your system is ready, login as a root and complete following steps:
Edit your /etc/hosts file and make sure it looks similar to this one:
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 192.168.0.45 post.example.com post ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
Edit network settings in /etc/sysconfig/network-scripts/ifcfg-eth0 file with vi text editor:
vi /etc/sysconfig/network-scripts/ifcfg-eth0
Make sure you have these lines in your network configuration file:
DEVICE="eth0" HWADDR="yo:ur:ma:ca:dd:re:ss" NM_CONTROLLED="no" ONBOOT="yes" TYPE="Ethernet" BOOTPROTO="static" IPADDR=192.168.0.45 NETMASK=255.255.255.0
Also you need to add a gateway and at least one DNS server to your network configuration. In order to do that first edit /etc/sysconfig/network file
vi /etc/sysconfig/network
and add these lines:
NETWORKING=yes HOSTNAME=post.example.com GATEWAY=192.168.0.1
Then edit /etc/resolv.conf file
vi /etc/resolv.conf
and add this line there:
search . nameserver 192.168.0.1
After all this is done restart network service:
/etc/init.d/network restart
You may run yum update command now to update the system.
To avoid some unnecessary headaches we have to disable SELinux and firewall for now. To do that, we can use nice system-config-firewall tool, but we need to install it first:
yum install system-config-firewall
and then run it:
system-config-firewall
Untick the option Enabled and click OK>Yes
In order to disable SELinux open /etc/selinux/config file and set SELINUX=disabled
vi /etc/selinux/config
Reboot the machine now:
reboot
Now, let’s install Graphic User Interface (GUI) for our server. You are free to skip this step if you are not interested in software that will need GUI.
I prefer XFCE GUI as it is light and elegant so I’ll install it on the server
yum install wget
wget http://download.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-7.noarch.rpm
rpm -ivh epel-release-6-7.noarch.rpm
yum groupinstall Xfce
yum install -y xorg-x11-fonts-*
If you start to receive some unresolvable host errors while executing yum commands (i.e. “…[Errno 14] PYCURL ERROR 6 – “Couldn’t resolve host…”) please make sure that /etc/resolv.conf and /etc/sysconfig/network files hasn’t been changed by NetworkManager and if so, repeat corresponding steps above and remove NetworkManager:
yum remove NetworkManager
To start CentOS in graphics mode, change /etc/inittab file and set the content of the file to id:5:initdefault:.
So now we have our mini system ready you are free to choose what else you want to install. As this article focuses on ESET’s solutions for Linux my main aim is to show how to make it working and how does it look like. I’ll try to achieve this by using Nginx web server, Postfix mail server, Courier IMAP server and ISPconfig 3 hosting control panel.
You may want to proceed to these howtos to make your server fully functional:
- The Perfect Server – CentOS 6.3 x86_64 (nginx, Courier, ISPConfig 3) – from step 7 OR
- The Perfect Server – CentOS 6.3 x86_64 (Apache2, Courier, ISPConfig 3) – from step 7
These apps will become useful should you go for one of options above:
yum install sudo unzip bzip2 unrar perl-DBD-mysql vixie-cron crontabs
/sbin/chkconfig crond on
/sbin/service crond start
NOTE: skip step 14 to avoid installation of clamav antivirus and amavisd-new mail virus scanner.
Installing ESET NOD32 4 for Linux Desktop (GUI must be used!)
Open Terminal and enter following command to download the latest NOD32 antivirus for Linux (64bit edition):
wget http://download.eset.com/download/unix/eav/eset_nod32av_64bit_en.linux
For Business Edition use this link:
wget http://download.eset.com/download/unix/eavbe/ueavbe.x86_64.en.linux
Make installation file executable:
chmod +x eset_nod32av_64bit_en.linux OR chmod +x ueavbe.x86_64.en.linux for Business Edition.
In order to run this file we also will need 32bit GNU libc libraries so let’s install them:
sudo yum install glibc.i686
And finally install it using this command:
./eset_nod32av_64bit_en.linux OR ./ueavbe.x86_64.en.linux for BE.
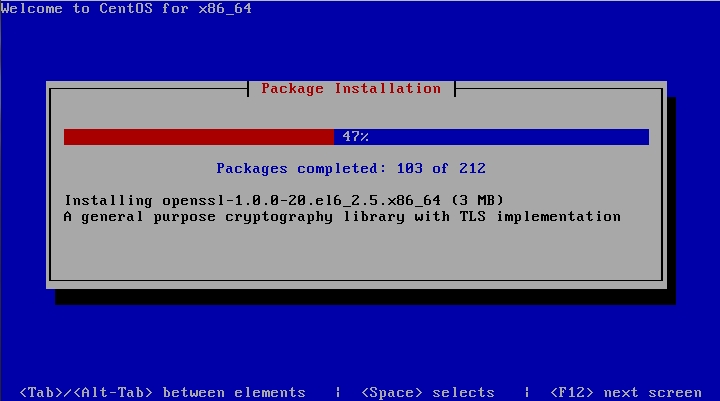
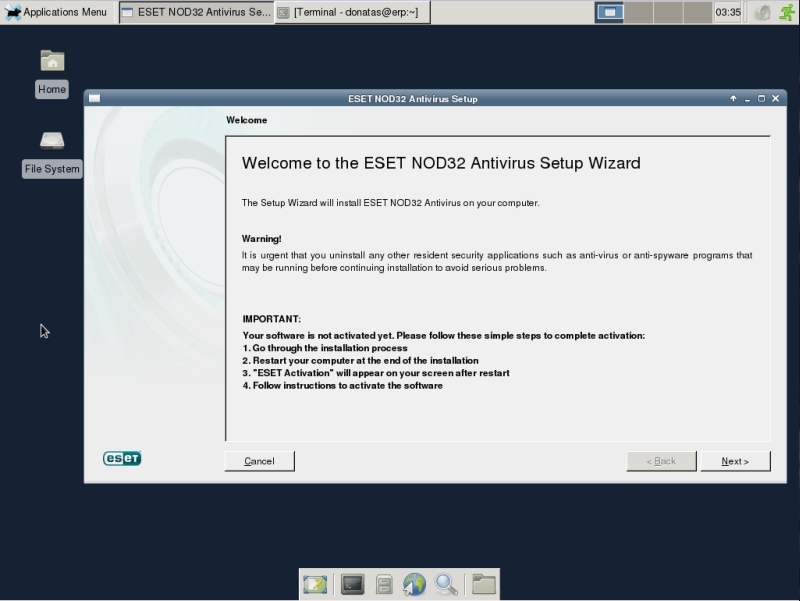
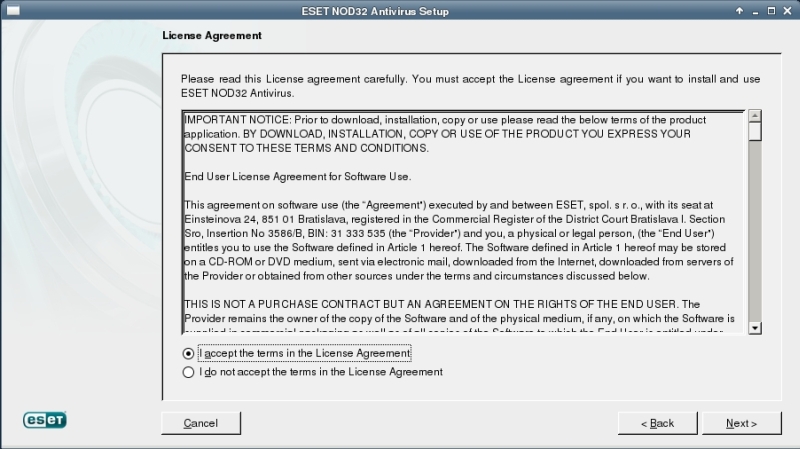
From now on you will see visual installation wizard. Gallery below shows installation progress.
Installation and configuration of ESET Mail Security for Linux
Installation
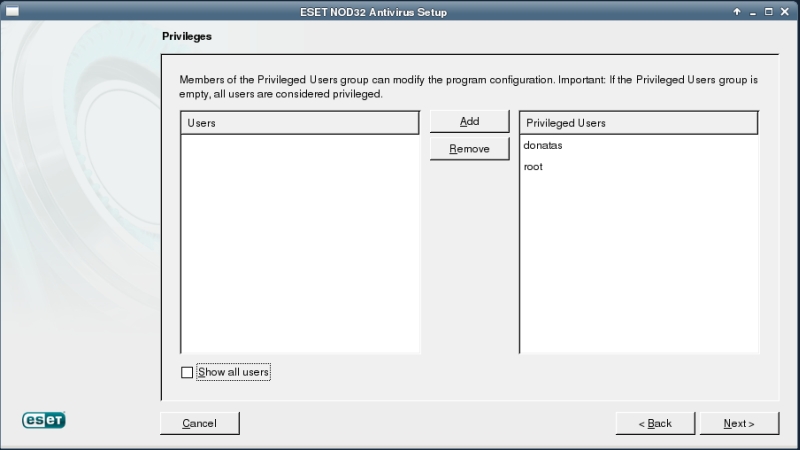
You have to remove previously installed ESET NOD32 for Linux before to proceed with this part of tutorial. Luckily, it’s very easy task to do – simply navigate to Applications Menu > System > ESET NOD32 Antivirus Uninstaller
You also will have to have a username and a password for a product you want to download. You may request a free trial from us if you don’t have them.
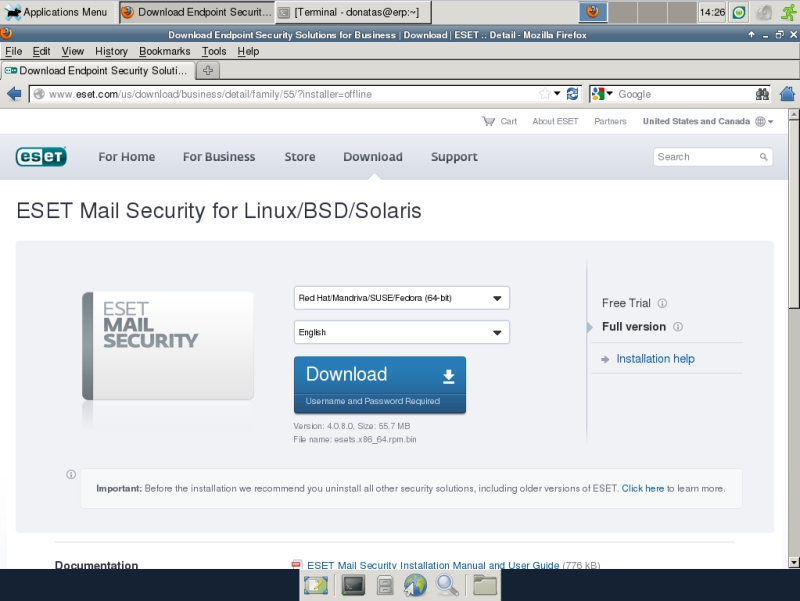
So let’s assume that you have a licence. ESET downloads page will request you the licence information, thus we need to access it through the browser – install the browser first:
sudo yum install firefox flash-plugin
After that just use your web browser (Firefox in this case) to get to ESET Mail Security for Linux download page. Pick Red Hat/Mandriva/SUSE/Fedora (64-bit) version, click Download, enter your username and password and save the file in your user’s home directory (in my case it’s /home/donatas). At the time of writing installation filename was esets.x86_64.rpm.bin.
Now in your terminal execute this command to create Mail Security’s RPM package for Red Hat© based Linux distributions:
sh ~/esets.x86_64.rpm.bin
Install some extra libraries:
sudo yum install ed
And then install the RPM package:
sudo rpm -U esets-4.0.8.x86_64.rpm
Now you have to upload/download your ESET licence file on the server. The file is usually packed in nod32.zip archive and it’s called nod32.lic. It should be attached to the registration/purchase confirmation email sent by ESET. I won’t discuss here the ways how you can get this file on your server, but just for consistency put it to your home directory.
Import the licence file:
sudo /opt/eset/esets/sbin/esets_lic --import ~/nod32.lic
Add your username and password to /etc/opt/eset/esets/esets.cfg file in [global] section under ESETS Update options:
sudo vi /etc/opt/eset/esets/esets.cfg
It should look like this now:
# av_update_username = "username" # Username used in authentication against ESET server. av_update_username = "EAV-1234567" # av_update_password = "password" # Password used in authentication against ESET server. av_update_password = "fdsd763dd"
And finally start ESET daemon:
sudo /etc/init.d/esets start
Check if daemon has startded:
ps -C esets_daemon
You should see the following lines:
PID TTY TIME CMD 2616 ? 00:00:00 esets_daemon 2618 ? 00:00:05 esets_daemon
Should you wish to uninstall ESET Mail Security for Linux run this command in Terminal:
sudo rpm -e esets
Configuration
Let’s make the hard life of server’s admin easier by enabling web interface which allows user friendly configuration. And once again we have to modify ESET configuration file:
sudo vi /etc/opt/eset/esets/esets.cfg
Get down to [wwwi] section and make it look like this:
[wwwi] # Settings for ESETS Web Interface configuration module # agent_enabled = yes/no # Enables operation of the esets_wwwi. agent_enabled = yes # listen_addr = "address" # Address (IP or name) where esets_wwwi listens for HTTPS client connections. # If set to 0.0.0.0 then esets_wwwi listens on all available network interfaces. listen_addr = "192.168.0.45" # listen_port = port # TCP port where esets_wwwi listens for HTTPS client connections. # You may have to open this port in your firewall. listen_port = 3377 # username and password needed for accessing the interface (required) username = "eset_adm" password = "yourStrongPassword"
We wont be able to access the web interface unless we will open our chosen port in firewall or in this case in ISPconfig’s firewall configuration section. So login to your ISPconfig panel (https://localhost:8080, default: admin/admin) and go to System > Firewall (Basic) > Add Firewall record. Add the chosen port (3377) to Open TCP ports field and click Save. Then restarts esets daemon
sudo /etc/init.d/esets restart
and use https://192.168.0.45:3377 URL to access your ESET web interface.
Now it’s time to make ESET and Postfix live nicely together.
Since we did not installed amavis we still have to remove any references to it in Postfix main.cf and master.cf files, otherwise email will stuck in a queue producing errors such as “connect to 127.0.0.1[127.0.0.1]:10024: Connection refused” and “warning: connect to transport private/amavis: Connection refused”
Open main.cf file,
sudo vi /etc/postfix/main.cf
comment following lines
#content_filter = amavis:[127.0.0.1]:10024 #receive_override_options = no_address_mappings
and add this line below them
mailbox_command = /usr/bin/maildrop
or otherwise you will receive this error during the installation: “Postfix inbound install using esets_mda: No file procmail in…”
Do similar thing with master.cf file:
sudo vi /etc/postfix/master.cf
#amavis unix - - - - 2 smtp # -o smtp_data_done_timeout=1200 # -o smtp_send_xforward_command=yes #127.0.0.1:10025 inet n - - - - smtpd # -o content_filter= # -o local_recipient_maps= # -o relay_recipient_maps= # -o smtpd_restriction_classes= # -o smtpd_client_restrictions= # -o smtpd_helo_restrictions= # -o smtpd_sender_restrictions= # -o smtpd_recipient_restrictions=permit_mynetworks,reject # -o mynetworks=127.0.0.0/8 # -o strict_rfc821_envelopes=yes # -o receive_override_options=no_unknown_recipient_checks,no_header_body_checks # -o smtpd_bind_address=127.0.0.1
Now restart Postfix and re-queue existing messages:
sudo /etc/init.d/postfix restart
sudo postsuper -r ALL
I recommend you to try send and receive email over POP3/IMAP/SMTP using current configuration. In that way you will know that it was working before ESET software changed Postfix configuration files. However, ESET also makes a backup of these files and allows to restore it easily.
Let’s enable inbound message scanning now.
Run in Terminal:
sudo /opt/eset/esets/sbin/esets_setup
Select MTA option and pick the first option after. All this should look like this:
[donatas@erp ~]$ sudo /opt/eset/esets/sbin/esets_setup [sudo] password for donatas: Welcome to esets_setup, the ESET Security interactive automated install script. It will help you integrate ESET Security with your system easily and can later undo all changes. In case some files must be modified, they will be backed up in your home directory. There are no automated installations for File Servers, see the guide in /opt/eset/esets/share/doc for general instructions. Do you want to see commands, which will be executed during installation? (y/n, default=y) Available ESETS installations/uninstallations: 1) MTA 2) POP3 3) IMAP 4) SMTP 5) HTTP 6) FTP 7) ICAP 8) quit Your selection (1-8): 1 Select MTA install/uninstall: 1) Postfix inbound install using esets_mda: tar cf $HOME/esets_backup-20120814-205345.tar -C / 'etc/opt/eset/esets/esets.cfg' -C / 'etc/postfix/main.cf' && /opt/eset/esets/sbin/esets_set --section mda 'mda_path = "/usr/bin/maildrop"' && /etc/init.d/esets restart && echo '#esets orig mboxcmd: /usr/bin/maildrop' >> '/etc/postfix/main.cf' && /usr/sbin/postconf -e 'mailbox_command = /opt/eset/esets/bin/esets_mda -- --recipient="$RECIPIENT" --sender="$SENDER"' && /etc/rc.d/init.d/postfix reload 2) Postfix contentfilter install using esets_smtp: tar cf $HOME/esets_backup-20120814-205345.tar -C / 'etc/opt/eset/esets/esets.cfg' -C / 'etc/postfix/main.cf' -C / 'etc/postfix/master.cf' && /opt/eset/esets/sbin/esets_set --section smtp 'agent_enabled = yes' && /opt/eset/esets/sbin/esets_set --section smtp 'listen_addr = localhost' && /opt/eset/esets/sbin/esets_set --section smtp 'listen_port = 2526' && /opt/eset/esets/sbin/esets_set --section smtp 'server_addr = localhost' && /opt/eset/esets/sbin/esets_set --section smtp 'server_port = 2525' && /etc/init.d/esets restart && printf 'localhost:2525 inet n - n - - smtpd\n -o content_filter=\n -o myhostname=esets.example.com\n -o local_recipient_maps=\n -o relay_recipient_maps=\n -o receive_override_options=no_unknown_recipient_checks,no_header_body_checks\n -o smtpd_helo_restrictions=\n -o smtpd_client_restrictions=\n -o smtpd_sender_restrictions=\n -o smtpd_recipient_restrictions=permit_mynetworks,reject\n -o mynetworks=127.0.0.0/8\n' >> '/etc/postfix/master.cf' && /usr/sbin/postconf -e 'content_filter = smtp:[127.0.0.1]:2526' && /etc/rc.d/init.d/postfix reload 3) quit Your selection (1-3): 1 Restarting ESET Security [ OK ] Reloading postfix: [ OK ]
Now add
content_filter = smtp:[127.0.0.1]:2526
line to the main.cf file:
sudo vi /etc/postfix/main.cf
And lines
localhost:2525 inet n - n - - smtpd -o content_filter= -o myhostname=post.example.com -o local_recipient_maps= -o relay_recipient_maps= -o receive_override_options=no_unknown_recipient_checks,no_header_body_checks -o smtpd_helo_restrictions= -o smtpd_client_restrictions= -o smtpd_sender_restrictions= -o smtpd_recipient_restrictions=permit_mynetworks,reject -o mynetworks=127.0.0.0/8
to the master.cf file. Change myhostname to your hostname.
sudo vi /etc/postfix/master.cf
To avoid editing esets.cfg file let’s use web interface and change settings there. Login to you web interface (https://192.168.0.45:3377) and open MDA configuration – Configuration > MDA.
As you can see, web interface offers many configuration options, but let’s focus on a simplest ones just to make sure system is working. Once you are sure, you can play with the settings and adjust them to your needs.
Here is the list what I activated on MDA page:
- MDA path = /usr/bin/maildrop
- Anti-Spam action = scan
- SPAM subject prefix = **SPAM**
- Spam threshold = 90
- Likely ham threshold = 50
- Ham threshold = 10
Set only these values for now and click Save changes on the bottom and Apply changes on left menu.
Now move to SMTP section and make following changes there too:
- Listen address = localhost
- Listen port = 2526
- Server address = localhost
- Server port = 2525
- Enable agent = yes
- Anti-Spam action = scan
- Spam subject prefix = ***SPAM***
And once again click Save changes on the bottom and Apply changes on left menu.
Restart esets daemon and reload Postfix:
sudo /etc/init.d/esets restart
sudo /etc/init.d/postfix reload
To test if ESET spam filter is working properly send the message to your server from the domain on different server with the body
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X
in it.
The message should get ***SPAM*** mark from ESET Mail Security and end up in Junk folder.
With this configuration ESET Mail Security will also check for infected mail messages and inform the sender about undelivered mail:
[..]: host 127.0.0.1[127.0.0.1] said: 550 Rejected by ESETS_SMTP (infected) (in reply to end of DATA command)
For more customization options please refer to ESET Mail Security Installation Guide and Manual.
Configuring ESET File Security for Linux
Dazuko, Dazuko… Yes, I’m going to skip it here, but you can try it out on a newest CentOS kernel and share your results.
My aim here is to show how to use scheduled (on-demand scanner) ESETS file scanning of your users’ web and FTP directories. ESET Mail Security takes care of viruses and spam in your email anyway.
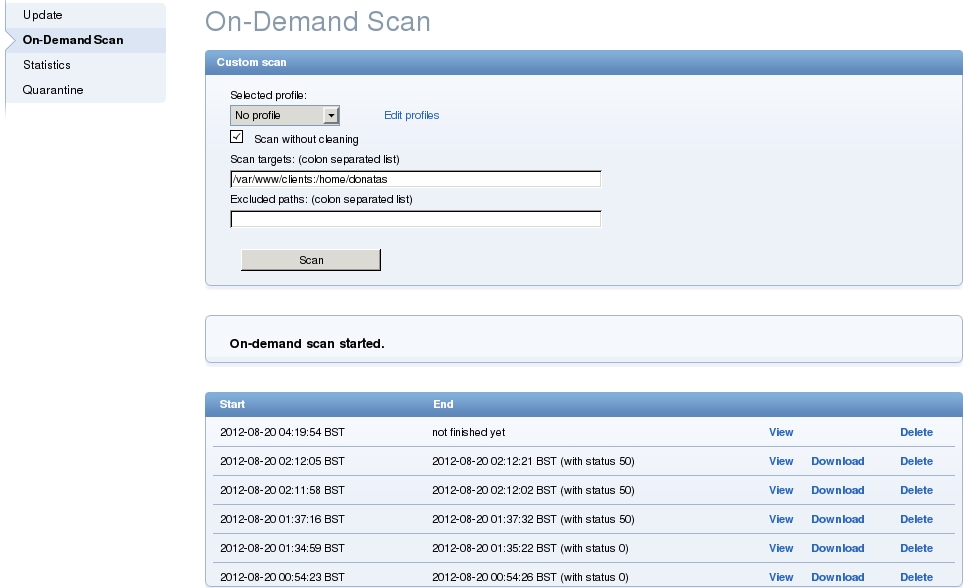
Option 1 – Run scanner manually through the ESETS web interface
Login to your ESET Server Security web interface, which you set at previous stage (https://192.168.0.45:3377). Go to Control > On-Demand Scan, enter /var/www/clients to the Scan targets input field and click Scan. After some time, depending of size of target directory, you will see View/Download links to the scan report.
Should you wish to add more directories simply use colon (:) to separate them.
Here is how scan report looks like (I intentionally put infected file there):
ESET Command-line scanner, version 4.0.8, (C) 1992-2010 ESET, spol. s r.o. Using license: Donatas (/etc/opt/eset/esets/license/esets_c786df.lic) Module loader, version 1040 (20120313), build 1048 Module perseus, version 1365 (20120724), build 1486 Module scanner, version 7399 (20120819), build 11898 Module archiver, version 1149 (20120808), build 1115 Module advheur, version 1121 (20111208), build 1081 Module cleaner, version 1057 (20120626), build 1065 Command line: -- /var/www/clients /home/donatas Scan started at: Mon 20 Aug 2012 01:37:19 AM BST name="/var/www/clients/client1/web1/web/nastyFile.exe", threat="probably a variant of Win32/Agent.SOMENAME trojan", action="unable to clean", info="" name="/var/www/clients/client1/web1/web/nastyFile.exe » RAR » Setup.exe", threat="probably a variant of Win32/Agent.SOMENAME trojan", action="unable to clean", info="" Scan completed at: Mon 20 Aug 2012 01:37:32 AM BST Scan time: 13 sec (0:00:13) Total: files - 1731, objects 3227 Infected: files - 1, objects 1 Cleaned: files - 0, objects 0
Option 2 – Add On-Demand Scanner task to the Scheduler
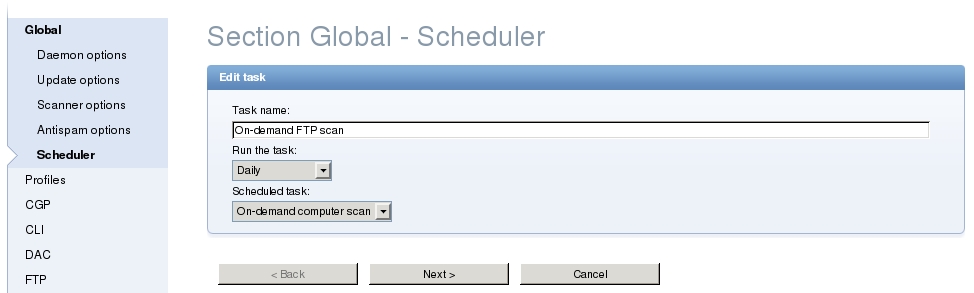
Navigate to Configuration > Scheduler and click the button Add New….
On a next screen give the task the name and set Run the task value to Daily and Scheduled task value to On-demand computer scan. Click Next.
Now set the time and tick the box Scan without cleaning if this is what you want. Add at least /var/www/clients to Scan targets field. Click Next, review the summary and click Finish. Do not forget to save and apply the changes too.
Option 3 – Add On-Demand Scanner task to crontab
Here is the full list of ESETS On-Demand Scanner command line options:
/home/donatas$ sudo /opt/eset/esets/sbin/esets_scan -h
ESET Security on-demand scanner
Syntax: esets_scan [OPTIONS..] FILES..
Options:
--exclude=MASK exclude files matching MASK from scanning
--subdir scan subfolders (default)
--no-subdir do not scan subfolders
--max-subdir-level=LEVEL maximum sub-level of folders within folders to
scan
-s, --symlink follow symbolic links (default)
--no-symlink skip symbolic links
--sysexclude automatically exclude system control
directories (default)
--no-sysexclude do not exclude system control directories
--ads scan ADS (default)
--no-ads do not scan ADS
-f, --log-file=FILE log output to FILE
--log-rewrite overwrite output file (default - append)
--log-console log output to console (default)
--no-log-console do not log output to console
-o, --log-all also log clean files
--no-log-all do not log clean files (default)
--scanlog=TASK:USER create a scan log with the TASK number and
USER
--aind show activity indicator
--auto scan and automatically clean all local disks
-p, --profile=PROFILE scan with selected PROFILE name
Scanner options:
--files scan files (default)
--no-files do not scan files
-z, --arch scan archives (default)
--no-arch do not scan archives
--max-obj-size=SIZE only scan files smaller than SIZE megabytes
(default 0 = unlimited)
--max-arch-level=LEVEL maximum sub-level of archives within archives
(nested archives) to scan
--scan-timeout=LIMIT scan archives for LIMIT seconds at maximum
--max-arch-size=SIZE only scan the files in an archive if they are
smaller than SIZE (default 0 = unlimited)
--max-sfx-size=SIZE only scan the files in a self-extracting
archive if they are smaller than SIZE
megabytes (default 0 = unlimited)
--mail scan email files (default)
--no-mail do not scan email files
--mailbox scan mailboxes (default)
--no-mailbox do not scan mailboxes
--sfx scan self-extracting archives (default)
--no-sfx do not scan self-extracting archives
--rtp scan runtime packers (default)
--no-rtp do not scan runtime packers
--adware scan for Adware/Spyware/Riskware (default)
--no-adware do not scan for Adware/Spyware/Riskware
--unsafe scan for potentially unsafe applications
--no-unsafe do not scan for potentially unsafe
applications (default)
--unwanted scan for potentially unwanted applications
--no-unwanted do not scan for potentially unwanted
applications (default)
--pattern use signatures (default)
--no-pattern do not use signatures
--heur enable heuristics (default)
--no-heur disable heuristics
-w, --adv-heur enable Advanced heuristics (default)
--no-adv-heur disable Advanced heuristics
--ext=EXTENSIONS scan only EXTENSIONS delimited by colon
--ext-exclude=EXTENSIONS exclude EXTENSIONS delimited by colon from
scanning
--clean-mode=MODE use cleaning MODE for infected objects.
Available options: none, standard (default),
strict, rigorous, delete
--quarantine copy infected files (if cleaned) to Quarantine
(supplements ACTION)
--no-quarantine do not copy infected files to Quarantine
General options:
-h, --help show help and quit
-v, --version show version information and quit
--preserve-time preserve last access timestamp
Exit codes:
0 no threat found
1 threat found and cleaned
10 some files could not be scanned (may be threats)
50 threat found
100 error
(C) 2012 ESET, spol. s r. o.
To report issues, please visit http://www.eset.com/support
In order to test the scanner, I’ll be using command below. You should see similar output as on example above.
sudo /opt/eset/esets/sbin/esets_scan --max-obj-size=5000 --no-mail --no-mailbox --clean-mode=none --quarantine /var/www/clients /home/donatas
What does it mean is that I don’t want any files to be scanned bigger than 5000 MB and I don’t want the antivirus to delete scanned files as it may include infected websites of my customers. All I want is the report. Should you wish to delete infected files, just use an option –clean-mode=delete and optionally the option –quarantine to send such files to quarantine for your later review at Control > Quarantine section in a web interface.
Please note, that the command line scanner must be executed as a privileged user (administrator), otherwise it won’t have enough rights to access certain files.
Now add this command to crontab. I want it to happen once a day, say, at midnight.
In terminal type:
sudo crontab -e
Add this line below other lines:
59 23 * * * /opt/eset/esets/sbin/esets_scan --no-log-console --max-obj-size=5000 --no-mail --no-mailbox --clean-mode=none --quarantine /var/www/clients /home/donatas
After all it should look like this:
* * * * * /usr/local/ispconfig/server/server.sh &> /dev/null 30 00 * * * /usr/local/ispconfig/server/cron_daily.sh &> /dev/null 0 0 * * * /usr/local/ispconfig/server/scripts/create_daily_nginx_access_logs.sh &> /dev/null 59 23 * * * /opt/eset/esets/sbin/esets_scan --no-log-console --max-obj-size=5000 --no-mail --no-mailbox --clean-mode=none --quarantine /var/www/clients /home/donatas
You also should receive email report after each scan to your root mail.
More information can be found in ESET File Security Installation manual.


































Comments
Share your opinion by posting or replying to others comments.
rozermartin –
April 11, 2014 at 11:07 - 10 years ago
I have gone through your Blog and found really a nice informative blog for antivirus support on Linux server. Your blog is easy to understand, and I really appreciate it.
Donatas Stonys –
April 11, 2014 at 12:46 - 10 years ago
Thank you, Martin 🙂 I will try to update it whenever I have some spare time.
Stefan –
March 29, 2013 at 15:52 - 11 years ago
Hi
I hope you can me a tip. I scan my Mails on ISPConfig once a week full with:
/opt/eset/esets/sbin/esets_scan –max-obj-size=5000 –clean-mode=none –quarantine /var/vmail
If it find something, it do not the files to the quarantine. Do you know why?
Thx
Stefan –
March 29, 2013 at 18:31 - 11 years ago
Hi all
The correct string must be as follow:
/opt/eset/esets/sbin/esets_scan –max-obj-size=5000 –no-mail –no-mailbox –quarantine /var/www/clients
-> no cleaning-mode
Stefan –
March 25, 2013 at 18:25 - 11 years ago
Hi
Thanks a lot for this tutorial. It’s scanning. May in my postfix queue hav I following errors:
18CA7A480AD 1931 Mon Mar 25 19:10:05 www-data@srv1.xxx
(temporary failure. Command output: local: fatal: execvp /usr/bin/maildrop: No such file or directory)
www-data@srv1.xxx
What could It be?
Thanks in advance
Stefan
Stefan –
March 29, 2013 at 18:36 - 11 years ago
ISPConfig has two setups:
One with courier and maildrop (this Howto) and the other with dovecot. I’ve a dovecot installation. I had set now in the eset configuration: MDA Path: /usr/lib/dovecot/deliver.
donatas –
March 29, 2013 at 19:28 - 11 years ago
Thank you for your comments, Stefan.
I’ve checked this setup carefully while I was preparing this how to, but unfortunately I’m too busy at the moment to replicate same setup and check if any issues exists, so once again, thank you very much for your feedback and possible solutions!
Steven Morrison –
September 10, 2012 at 15:19 - 12 years ago
I have a problem through the webinterface if i want to update the Mailserver i get an error message saying that the username and password is not correct. I did check the cfg file there it shows right. I did send the esets.cfg file to eset support and they said that the cfg file is correct as they can update there system with the file. I was wondering if there are any other places where this username and password could be saved .
donatas –
September 10, 2012 at 16:12 - 12 years ago
Hello Steven,
I think once I got this problem too. Did you try to go to Configuration > Update options, check the boxes for Username/Password (no other boxes should be checked, but make sure you enter correct username and password (twice)) and click on Save changes button and on Apply changes button after it?
ESETS daemon should restart, so give it several seconds and then go to Control > Update > click Update button and see what happens, I mean, what message will you receive below.
Hope this helps.